CryptoDB
Cryptanalysis of AES-PRF and Its Dual
| Authors: |
|
|---|---|
| Download: | |
| Presentation: | Slides |
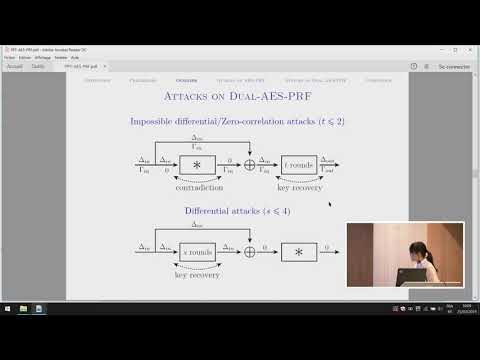
| Abstract: | A dedicated pseudorandom function (PRF) called AES-PRF was proposed by Mennink and Neves at FSE 2018 (ToSC 2017, Issue 3). AES-PRF is obtained from AES by using the output of the 5-th round as the feed-forward to the output state. This paper presents extensive security analysis of AES-PRF and its variants. Specifically, we consider unbalanced variants where the output of the s-th round is used as the feed-forward. We also analyze the security of “dual” constructions of the unbalanced variants, where the input state is used as the feed-forward to the output of the s-th round. We apply an impossible differential attack, zero-correlation linear attack, traditional differential attack, zero correlation linear distinguishing attack and a meet-in-the-middle attack on these PRFs and reduced round versions. We show that AES-PRF is broken whenever s ≤ 2 or s ≥ 6, or reduced to 7 rounds, and Dual-AES-PRF is broken whenever s ≤ 4 or s ≥ 8. Our results on AES-PRF improve the initial security evaluation by the designers in various ways, and our results on Dual-AES-PRF give the first insight to its security. |
Video from TOSC 2018
BibTeX
@article{tosc-2018-29233,
title={Cryptanalysis of AES-PRF and Its Dual},
journal={IACR Transactions on Symmetric Cryptology},
publisher={Ruhr-Universität Bochum},
volume={2018, Issue 2},
pages={161-191},
url={https://tosc.iacr.org/index.php/ToSC/article/view/892},
doi={10.13154/tosc.v2018.i2.161-191},
author={Patrick Derbez and Tetsu Iwata and Ling Sun and Siwei Sun and Yosuke Todo and Haoyang Wang and Meiqin Wang},
year=2018
}