CryptoDB
You Only Speak Once: Secure MPC with Stateless Ephemeral Roles
| Authors: |
|
|---|---|
| Download: |
|
| Conference: | CRYPTO 2021 |
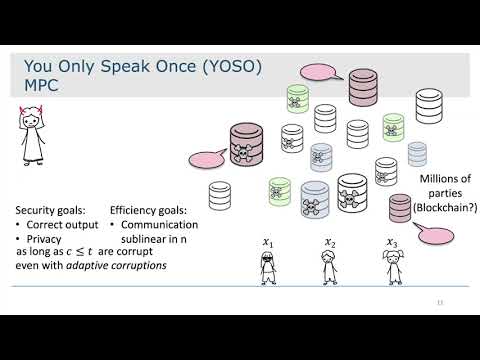
| Abstract: | The inherent difficulty of maintaining stateful environments over long periods of time gave rise to the paradigm of serverless computing, where mostly-stateless components are deployed on demand to handle computation tasks, and are teared down once their task is complete. Serverless architecture could offer the added benefit of improved resistance to targeted denial-of-service attacks, by hiding from the attacker the physical machines involved in the protocol until after they complete their work. Realizing such protection, however, requires that the protocol only uses stateless parties, where each party sends only one message and never needs to speaks again. Perhaps the most famous example of this style of protocols is the Nakamoto consensus protocol used in Bitcoin: A peer can win the right to produce the next block by running a local lottery (mining), all while staying covert. Once the right has been won, it is executed by sending a single message. After that, the physical entity never needs to send more messages. We refer to this as the You-Only-Speak-Once (YOSO) property, and initiate the formal study of it within a new model that we call the YOSO model. Our model is centered around the notion of roles, which are stateless parties that can only send a single message. Crucially, our modelling separates the protocol design, that only uses roles, from the role-assignment mechanism, that assigns roles to actual physical entities. This separation enables studying these two aspects separately, and our YOSO model in this work only deals with the protocol-design aspect. We describe several techniques for achieving YOSO MPC; both computational and information theoretic. Our protocols are synchronous and provide guaranteed output delivery (which is important for application domains such as blockchains), assuming honest majority of roles in every time step. We describe a practically efficient computationally-secure protocol, as well as a proof-of-concept information theoretically secure protocol. |
Video from CRYPTO 2021
BibTeX
@inproceedings{crypto-2021-31264,
title={You Only Speak Once: Secure MPC with Stateless Ephemeral Roles},
publisher={Springer-Verlag},
doi={10.1007/978-3-030-84245-1_3},
author={Craig Gentry and Shai Halevi and Hugo Krawczyk and Bernardo Magri and Jesper Buus Nielsen and Tal Rabin and Sophia Yakoubov},
year=2021
}