CryptoDB
Linear Cryptanalysis of FF3-1 and FEA
| Authors: |
|
|---|---|
| Download: |
|
| Presentation: | Slides |
| Conference: | CRYPTO 2021 |
| Award: | Best Paper by Early Career Researchers Award, Honorable mention for best paper |
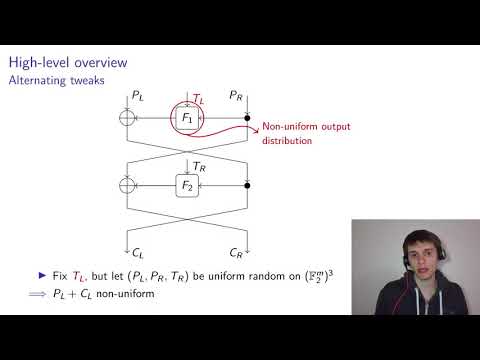
| Abstract: | Improved attacks on generic small-domain Feistel ciphers with alternating round tweaks are obtained using linear cryptanalysis. This results in practical distinguishing and message-recovery attacks on the United States format-preserving encryption standard FF3-1 and the South-Korean standards FEA-1 and FEA-2. The data-complexity of the proposed attacks on FF3-1 and FEA-1 is $O(N^{r/2 - 1.5})$, where $N^2$ is the domain size and $r$ is the number of rounds. For example, FF3-1 with $N = 10^3$ can be distinguished from an ideal tweakable block cipher with advantage $\ge 1/10$ using $2^{23}$ encryption queries. Recovering the left half of a message with similar advantage requires $2^{24}$ data. The analysis of FF3-1 serves as an interesting real-world application of (generalized) linear cryptanalysis over the group $\mathbb{Z}/N\mathbb{Z}$. |
Video from CRYPTO 2021
BibTeX
@inproceedings{crypto-2021-31097,
title={Linear Cryptanalysis of FF3-1 and FEA},
publisher={Springer-Verlag},
doi={10.1007/978-3-030-84242-0_3},
author={Tim Beyne},
year=2021
}