CryptoDB
Retrofitting Leakage Resilient Authenticated Encryption to Microcontrollers
| Authors: |
|
|---|---|
| Download: | |
| Presentation: | Slides |
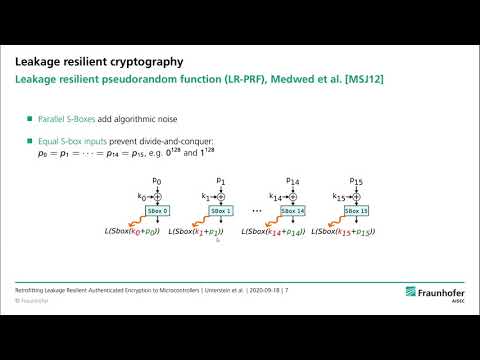
| Abstract: | The security of Internet of Things (IoT) devices relies on fundamental concepts such as cryptographically protected firmware updates. In this context attackers usually have physical access to a device and therefore side-channel attacks have to be considered. This makes the protection of required cryptographic keys and implementations challenging, especially for commercial off-the-shelf (COTS) microcontrollers that typically have no hardware countermeasures. In this work, we demonstrate how unprotected hardware AES engines of COTS microcontrollers can be efficiently protected against side-channel attacks by constructing a leakage resilient pseudo random function (LR-PRF). Using this side-channel protected building block, we implement a leakage resilient authenticated encryption with associated data (AEAD) scheme that enables secured firmware updates. We use concepts from leakage resilience to retrofit side-channel protection on unprotected hardware AES engines by means of software-only modifications. The LR-PRF construction leverages frequent key changes and low data complexity together with key dependent noise from parallel hardware to protect against side-channel attacks. Contrary to most other protection mechanisms such as time-based hiding, no additional true randomness is required. Our concept relies on parallel S-boxes in the AES hardware implementation, a feature that is fortunately present in many microcontrollers as a measure to increase performance. In a case study, we implement the protected AEAD scheme for two popular ARM Cortex-M microcontrollers with differing parallelism. We evaluate the protection capabilities in realistic IoT attack scenarios, where non-invasive EM probes or power consumption measurements are employed by the attacker. We show that the concept provides the side-channel hardening that is required for the long-term security of IoT devices. |
Video from TCHES 2020
BibTeX
@article{tches-2020-30558,
title={Retrofitting Leakage Resilient Authenticated Encryption to Microcontrollers},
journal={IACR Transactions on Cryptographic Hardware and Embedded Systems},
publisher={Ruhr-Universität Bochum},
volume={2020, Issue 4},
pages={365-388},
url={https://tches.iacr.org/index.php/TCHES/article/view/8687},
doi={10.13154/tches.v2020.i4.365-388},
author={Florian Unterstein and Marc Schink and Thomas Schamberger and Lars Tebelmann and Manuel Ilg and Johann Heyszl},
year=2020
}