CryptoDB
Investigating Profiled Side-Channel Attacks Against the DES Key Schedule
| Authors: |
|
|---|---|
| Download: | |
| Presentation: | Slides |
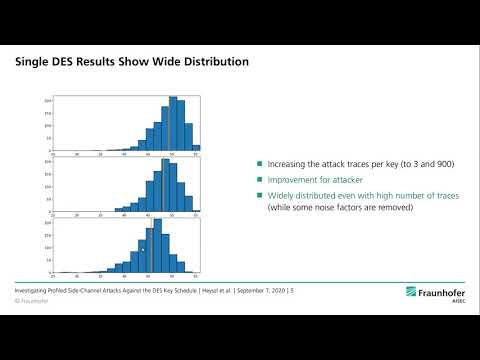
| Abstract: | Recent publications describe profiled single trace side-channel attacks (SCAs) against the DES key-schedule of a “commercially available security controller”. They report a significant reduction of the average remaining entropy of cryptographic keys after the attack, with surprisingly large, key-dependent variations of attack results, and individual cases with remaining key entropies as low as a few bits. Unfortunately, they leave important questions unanswered: Are the reported wide distributions of results plausible - can this be explained? Are the results device-specific or more generally applicable to other devices? What is the actual impact on the security of 3-key triple DES? We systematically answer those and several other questions by analyzing two commercial security controllers and a general purpose microcontroller. We observe a significant overall reduction and, importantly, also observe a large key-dependent variation in single DES key security levels, i.e. 49.4 bit mean and 0.9 % of keys < 40 bit (first investigated security controller; other results similar). We also observe a small fraction of keys with exceptionally low security levels that can be called weak keys. It is unclear, whether a device’s side-channel security should be assessed based on such rare weak key outliers. We generalize results to other leakage models by attacking the hardware DES accelerator of a general purpose microcontroller exhibiting a different leakage model. A highly simplified leakage simulation also confirms the wide distribution and shows that security levels are predictable to some extent. Through extensive investigations we find that the actual weakness of keys mainly stems from the specific switching noise they cause. Based on our investigations we expect that widely distributed results and weak outliers should be expected for all profiled attacks against (insufficiently protected) key-schedules, regardless of the algorithm and specific implementation. Finally, we describe a sound approach to estimate actual 3-key triple-DES security levels from empirical single DES results and find that the impact on the security of 3-key triple-DES is limited, i.e. 96.1 bit mean and 0.24 % of key-triples < 80 bit for the same security controller. |
Video from TCHES 2020
BibTeX
@article{tches-2020-30383,
title={Investigating Profiled Side-Channel Attacks Against the DES Key Schedule},
journal={IACR Transactions on Cryptographic Hardware and Embedded Systems},
publisher={Ruhr-Universität Bochum},
volume={2020, Issue 3},
pages={22-72},
url={https://tches.iacr.org/index.php/TCHES/article/view/8582},
doi={10.13154/tches.v2020.i3.22-72},
author={Johann Heyszl and Katja Miller and Florian Unterstein and Marc Schink and Alexander Wagner and Horst Gieser and Sven Freud and Tobias Damm and Dominik Klein and Dennis Kügler},
year=2020
}