CryptoDB
Asymmetric PAKE with low computation and communication
| Authors: |
|
|---|---|
| Download: | |
| Presentation: | Slides |
| Conference: | EUROCRYPT 2022 |
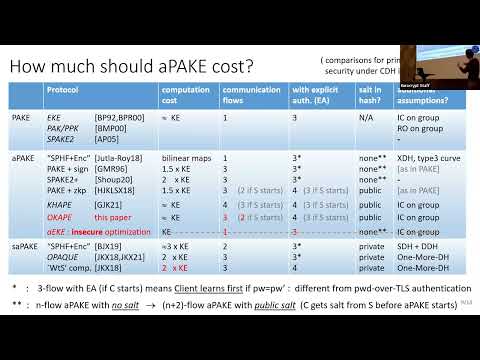
| Abstract: | In Crypto'21 Gu, Jarecki, and Krawczyk [20] showed an asymmetric password authenticated key exchange protocol (aPAKE) whose computational cost matches (symmetric) password authenticated key exchange (PAKE) and plain (i.e. unauthenticated) key exchange (KE). However, this minimal-cost aPAKE did not match prior aPAKE's in round complexity, using 4 rounds assuming the client initiates compared to 2 rounds in an aPAKE of Bradley et al. In this paper we show two aPAKE protocols that achieve optimal computational cost and optimal round complexity. Our protocols can be seen as applications of the Encrypted Key Exchange (EKE) compiler of Bellovin and Merritt [6], which creates password-authenticated key exchange by password-encrypting messages in a key exchange protocol. Whereas Bellovin and Merritt used this method to construct a PAKE by applying password-encryption to KE messages, we construct an aPAKE by applying password-encryption to messages of a unilaterally authenticated Key Exchange (ua-KE). We present two versions of this compiler. The first uses salted password hash and takes 3 rounds if the client initiates. The second uses unsalted password hash and takes a single simultaneous flow (it is the first aPAKE to do so), thus simultaneously matching the minimal computational cost and the minimal round complexity of PAKE and KE. We analyze our aPAKE protocols assuming Ideal Cipher (IC) on a group as modular constructions from ua-KE realized via a (universally composable) Authenticated Key Exchange where the server uses one-time keys (otk-AKE). We then show that one-pass variants of 3DH and HMQV securely realize otk-AKE in ROM. Interestingly, the two resulting concrete aPAKE's use the exact same protocol messages as two natural variants of EKE, and the only difference between the symmetric PAKE (EKE) and asymmetric PAKE (our protocols) is in the key derivation equation used to derive the final session key output. |
Video from EUROCRYPT 2022
BibTeX
@inproceedings{eurocrypt-2022-31939,
title={Asymmetric PAKE with low computation and communication},
publisher={Springer-Verlag},
author={Stanislaw Jarecki and Yanqi Gu and Bruno Freitas Dos Santos and Hugo Krawczyk},
year=2022
}