CryptoDB
Diving Deep into the Weak Keys of Round Reduced Ascon
| Authors: |
|
|---|---|
| Download: | |
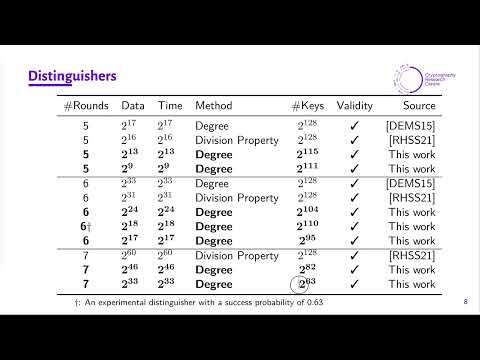
| Abstract: | At ToSC 2021, Rohit et al. presented the first distinguishing and key recovery attacks on 7 rounds Ascon without violating the designer’s security claims of nonce-respecting setting and data limit of 264 blocks per key. So far, these are the best attacks on 7 rounds Ascon. However, the distinguishers require (impractical) 260 data while the data complexity of key recovery attacks exactly equals 264. Whether there are any practical distinguishers and key recovery attacks (with data less than 264) on 7 rounds Ascon is still an open problem.In this work, we give positive answers to these questions by providing a comprehensive security analysis of Ascon in the weak key setting. Our first major result is the 7-round cube distinguishers with complexities 246 and 233 which work for 282 and 263 keys, respectively. Notably, we show that such weak keys exist for any choice (out of 64) of 46 and 33 specifically chosen nonce variables. In addition, we improve the data complexities of existing distinguishers for 5, 6 and 7 rounds by a factor of 28, 216 and 227, respectively. Our second contribution is a new theoretical framework for weak keys of Ascon which is solely based on the algebraic degree. Based on our construction, we identify 2127.99, 2127.97 and 2116.34 weak keys (out of 2128) for 5, 6 and 7 rounds, respectively. Next, we present two key recovery attacks on 7 rounds with different attack complexities. The best attack can recover the secret key with 263 data, 269 bits of memory and 2115.2 time. Our attacks are far from threatening the security of full 12 rounds Ascon, but we expect that they provide new insights into Ascon’s security. |
Video from TOSC 2021
BibTeX
@article{tosc-2021-31682,
title={Diving Deep into the Weak Keys of Round Reduced Ascon},
journal={IACR Transactions on Symmetric Cryptology},
publisher={Ruhr-Universität Bochum},
volume={2021, Issue 4},
pages={74-99},
url={https://tosc.iacr.org/index.php/ToSC/article/view/9329},
doi={10.46586/tosc.v2021.i4.74-99},
author={Raghvendra Rohit and Santanu Sarkar},
year=2021
}