CryptoDB
Succinct Non-Interactive Secure Computation
| Authors: |
|
|---|---|
| Download: |
|
| Conference: | EUROCRYPT 2020 |
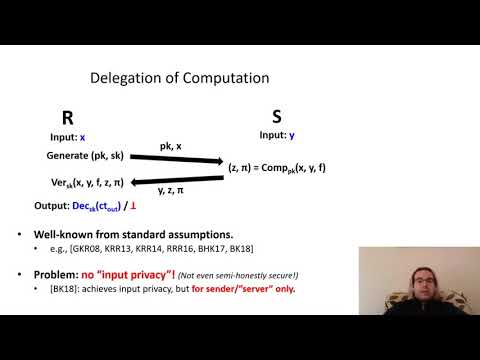
| Abstract: | We present the first maliciously secure protocol for succinct non-interactive secure two-party computation (SNISC): Each player sends just a single message whose length is (essentially) independent of the running time of the function to be computed. The protocol does not require any trusted setup, satisfies superpolynomial-time simulation-based security (SPS), and is based on (subexponential) security of the Learning With Errors (LWE) assumption. We do not rely on SNARKs or "knowledge of exponent"-type assumptions. Since the protocol is non-interactive, the relaxation to SPS security is needed, as standard polynomial-time simulation is impossible; however, a slight variant of our main protocol yields a SNISC with polynomial-time simulation in the CRS model. |
Video from EUROCRYPT 2020
BibTeX
@inproceedings{eurocrypt-2020-30252,
title={Succinct Non-Interactive Secure Computation},
booktitle={39th Annual International Conference on the Theory and Applications of Cryptographic Techniques, Zagreb, Croatia, May 10–14, 2020, Proceedings},
series={Lecture Notes in Computer Science},
publisher={Springer},
keywords={two-party computation;succinct;non-interactive;quasi-polynomial simulation;malicious security},
volume={12105},
doi={10.1007/978-3-030-45724-2_8},
author={Andrew Morgan and Rafael Pass and Antigoni Polychroniadou},
year=2020
}