CryptoDB
Denial-of-Service on FPGA-based Cloud Infrastructures — Attack and Defense
| Authors: |
|
|---|---|
| Download: | |
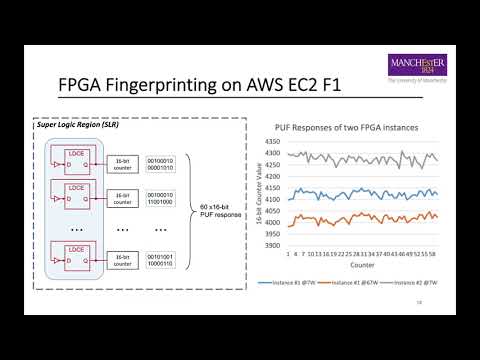
| Abstract: | This paper presents attacks targeting the FPGAs of AWS F1 instances at the electrical level through power-hammering, where excessive dynamic power is used to crash FPGA instances. We demonstrate different power-hammering attacks that pass all AWS security fences implemented on F1 instances, including the FPGA vendor design rule checks. In addition, we fingerprint the FPGA instances to observe the responsiveness of the instances, which indicates a successful denial-of-service attack. Most importantly, we provide an FPGA virus scanner framework, which was improved to support large datacenter FPGAs for preventing such attacks, including virtually all currently demonstrated side-channel attacks. Our experiments showed that an AWS F1 instance crashes immediately by starting an FPGA design demanding 369W. By using FPGA-fingerprinting, we found that crashed instances are unavailable for about one to over 200 hours. |
Video from TCHES 2021
BibTeX
@article{tches-2021-31291,
title={Denial-of-Service on FPGA-based Cloud Infrastructures — Attack and Defense},
journal={IACR Transactions on Cryptographic Hardware and Embedded Systems},
publisher={Ruhr-Universität Bochum},
volume={2021, Issue 3},
pages={441-464},
url={https://tches.iacr.org/index.php/TCHES/article/view/8982},
doi={10.46586/tches.v2021.i3.441-464},
author={Tuan La and Khoa Pham and Joseph Powell and Dirk Koch},
year=2021
}