CryptoDB
Handling Adaptive Compromise for Practical Encryption Schemes
| Authors: |
|
|---|---|
| Download: |
|
| Conference: | CRYPTO 2020 |
| Award: | Early Career Researcher Award |
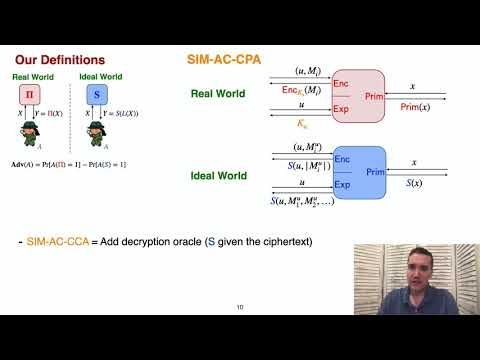
| Abstract: | We provide a new definitional framework capturing the multi-user security of encryption schemes and pseudorandom functions in the face of adversaries that can adaptively compromise users' keys. We provide a sequence of results establishing the security of practical symmetric encryption schemes under adaptive compromise in the random oracle or ideal cipher model. The bulk of analysis complexity for adaptive compromise security is relegated to the analysis of lower-level primitives such as pseudorandom functions. We apply our framework to give proofs of security for the BurnBox system for privacy in the face of border searches and the in-use searchable symmetric encryption scheme due to Cash et al. In both cases, prior analyses had bugs that our framework helps avoid. |
Video from CRYPTO 2020
BibTeX
@inproceedings{crypto-2020-30496,
title={Handling Adaptive Compromise for Practical Encryption Schemes},
publisher={Springer-Verlag},
doi={10.1007/978-3-030-56784-2_1},
author={Joseph Jaeger and Nirvan Tyagi},
year=2020
}